OWASP Top10 TryHackMe Notes

OWASP, or the Open Web Application Security Project is a nonprofit foundation launched in 2001, that works to improve the security of software in an open community setting. It was incorporated as a non-profit charity in April of 2004 and the goal is to enable organizations to maintain trusted applications
- Injection Vulnerabilities
One of the more older bugs on the list, injection vulnerabilities happen when user input gets translated as an actual command or parameter by an application. It basically tricks apps into spewing out commands they shouldn't. In short, it's like passing a fake ID off at a bar and getting whatever drink you'd like in return. TryHackMe lists off a few examples, but I added a few more to this list:
Examples:
• SQL Injections: Passing queries can manipulate outcome
• LDAP: Uses LDAP statements to exploit apps based on input
• XML (XPATH): XPATH queries utilize XML to pass information
• Command Injection: When input is passed to system commands
In the TryHackMe exercise, you can see that anything you input in the example gives up information:
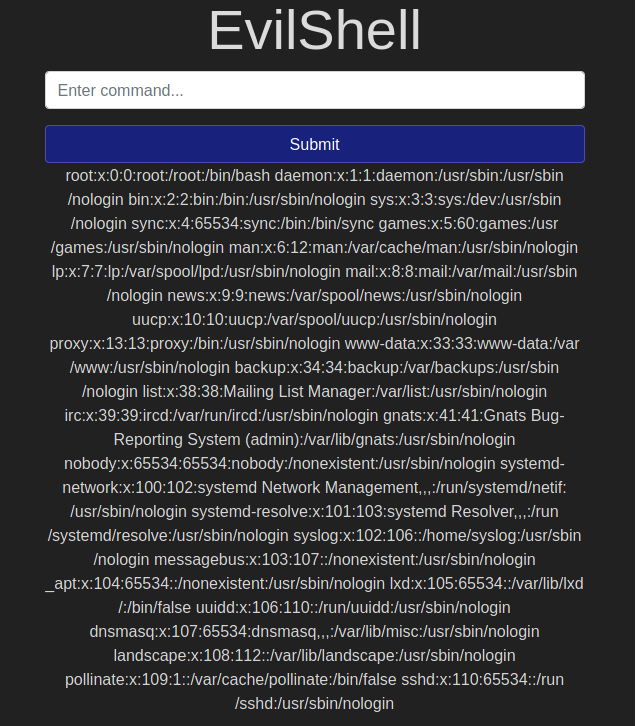
Mitigation:
Ensuring input isn't interpreted as a query/command which can be done with an allow list that compares the input as safe or rejected, or by stripping any input that contains dangerous characters and removing them.
2. Broken Authentication
Authentication verifies identity (think username/password) and if there are flaws within how it's done, you could potentially gain access to accounts and data you shouldn't have.
Examples:
• Brute force attacks
• Weak passwords
• Session Cookies: If they contain predictable values, you could set your own
In TryHackMe's example, you create a user called (_)darren with a space before the name, so even though the username darren is taken, you end up logging into the account.
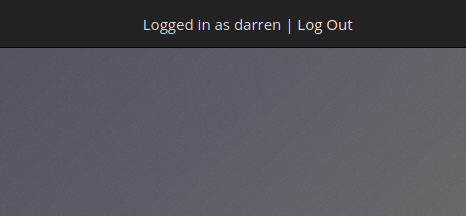
Mitigation:
• Enforce a strong password policy and an automatic lockout after a # of attempts
• Implement MFA
3. Sensitive Data Exposure
Happens when a webapp accidentally gives up data, generally customer info, or usernames/passwords. This category can and does include MiTM attacks.
4. XXE: XML External Entity:
Abuses XML parsers/data and often allows an attacker to interact with backend/external systems. Includes in-band and out-of-band XXE (blind).
When XXE is In-band, the attacker can receive immediate responses to a payload, but when it's out-of-band, the attacker has to reflect the payload output to their own server.
Examples:
• Server-Side Request Forgery (SSRF)
5. Broken Access Controls:
Basically, if a user can access protected pages they aren't supposed to, the controls aren't working. This can lead to sensitive data being leaked.
6. Security Misconfigurations:
Refers to things like badly configured permissions on cloud services like S3 buckets.
7. XSS (Cross-Site Scripting) Vulnerabilities
A type of injection that allows an attacker to execute malicious scripts and have it execute on a victim’s machine when user input isn't sanitized. These bugs can be found in JavaScript, VBScript, Flash and CSS, and they are categorized into 3 sections. Stored, Reflected and DOM based.
8. Insecure Deserialization:
Replaces data processed by an application with malicious code and allows anything from a DoS to an RCE to be used based on the attacker's skill.
9. Components with known vulnerabilities (self-explanatory)
10. Insufficient Logging/Monitoring
Logging should always be enabled. acker performed if they gain access to particular web applications. Without it, an attacker could go on undetected for a while. Monitoring should also be in place to detect anything suspicious.
If you'd like to brush up on your OWASP skills, check the following room from THM! It's great!


