Note Taking Presentation




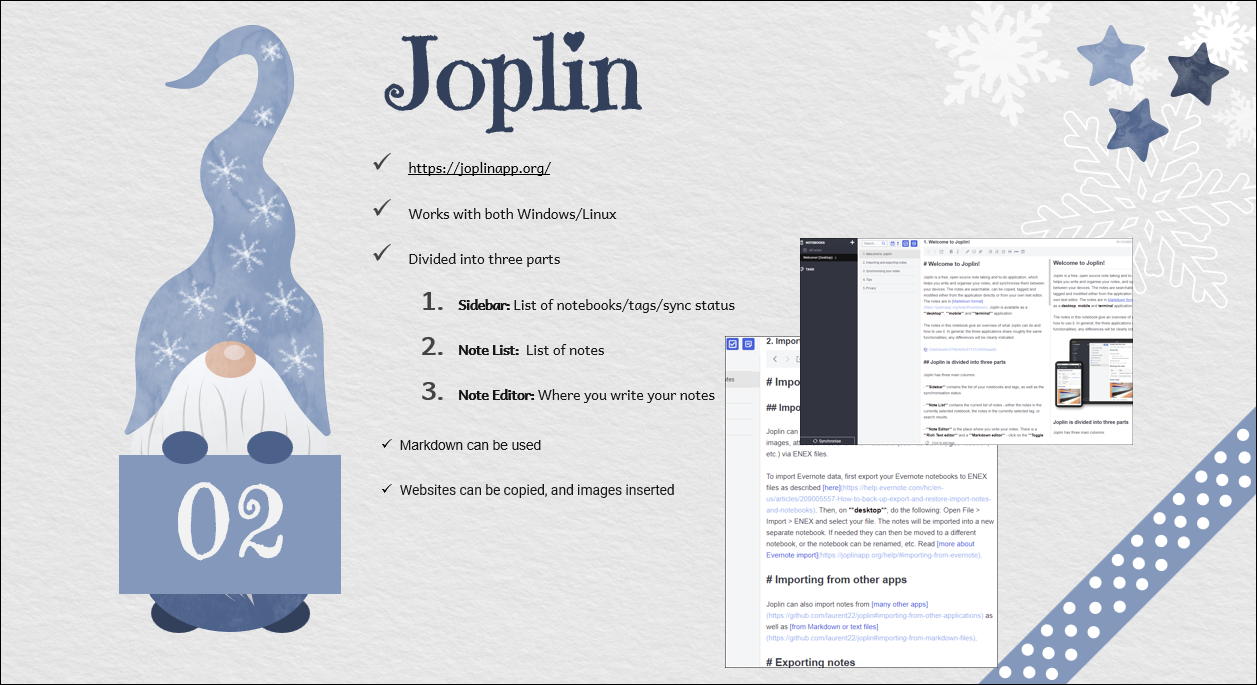
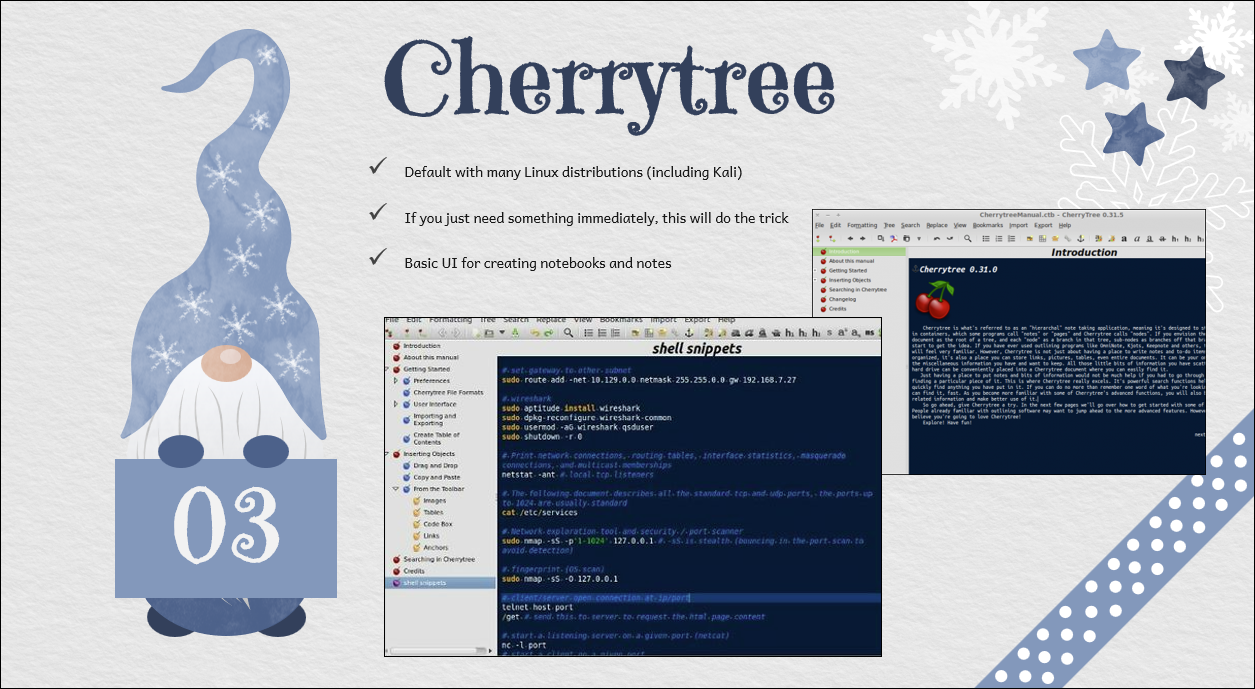
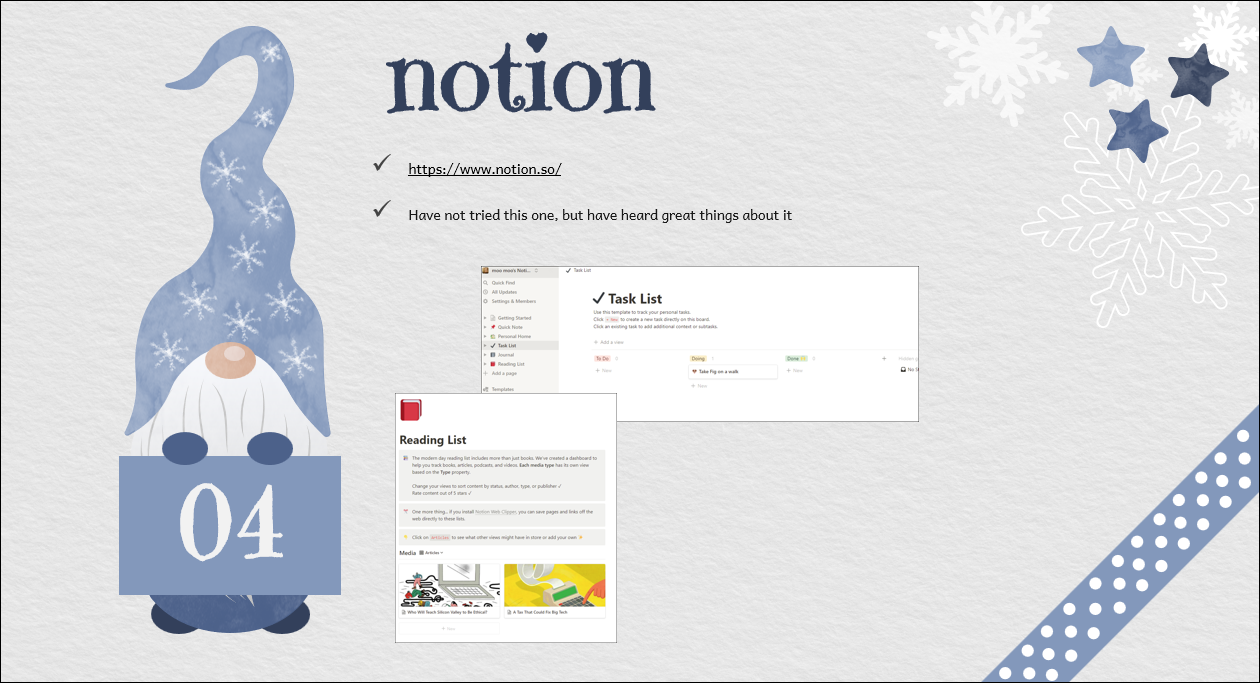
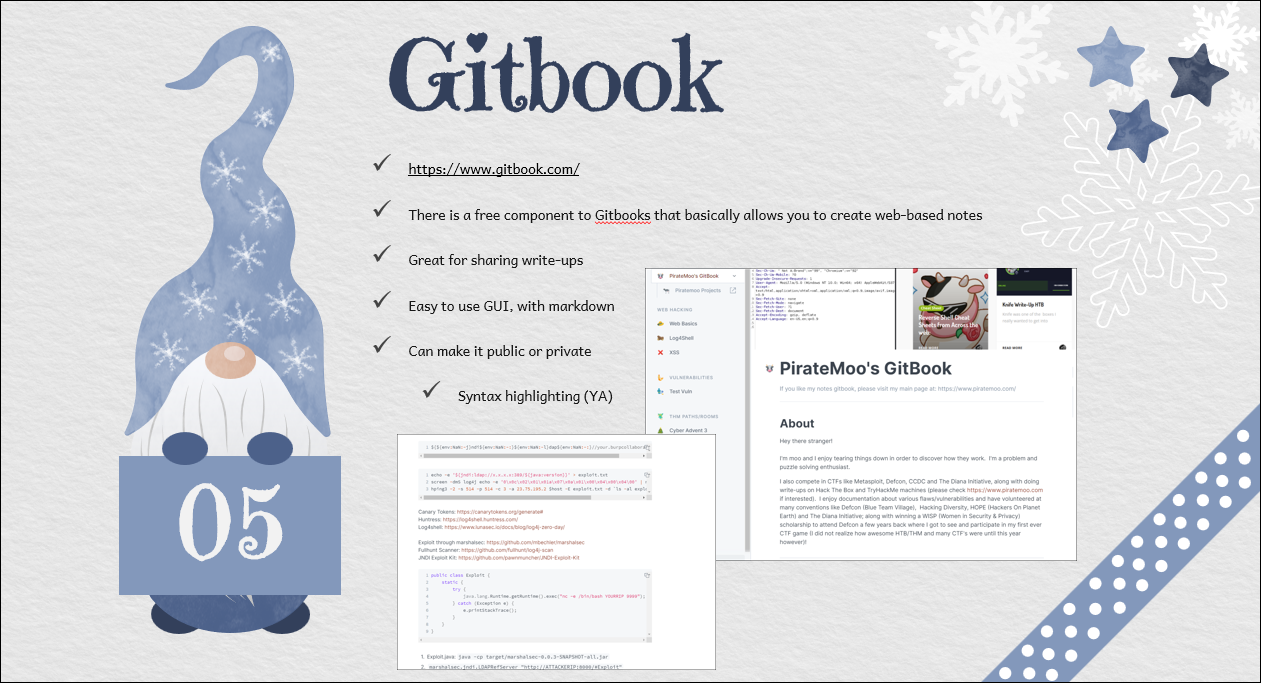

Additional: I use the Cornell note taking method. You can find out more here: https://en.wikipedia.org/wiki/Cornell_Notes










Additional: I use the Cornell note taking method. You can find out more here: https://en.wikipedia.org/wiki/Cornell_Notes
