Rapid SSL Assessments for Typical Discoveries in PenTests
This three-part series is intended to provide clarity on frequently encountered SSL-related issues in penetration tests. It includes a brief explanation of attacks, resources, and a cheat-sheet for quick validation in part two.

Part 1
This three-part series is intended to provide clarity on frequently encountered SSL-related issues in penetration tests. It includes a brief explanation of attacks, resources, and a cheat-sheet for quick validation in part two.
Many prefer not to allocate significant amounts of time to these issues during a penetration test, so I will discuss efficient methods for rapid validation if it's required on a given engagement.
NOTE: The majority of these findings often carry lower priority, contingent upon a client's specific threat model. Nonetheless, having a solid foundation of these concepts is valuable knowledge, even if a majority of them are MITM (Man-in-the-Middle) based.
BEAST: Browser Exploit Against SSL/TLS

CVE: CVE-2011-3389
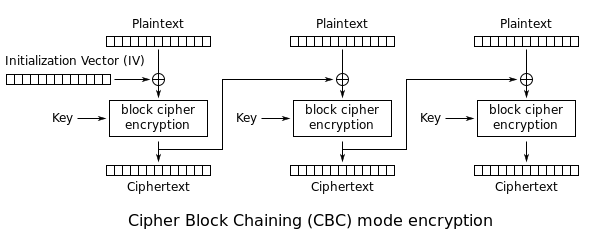
BEAST attacks SSL 3.0 and TLS 1.0 by exploiting CVE-2011-3389 where the vulnerability lies within the implementation of CBC (Cipher Block Chaining) in TLS 1.0, which allows an attacker to decrypt encrypted data between two users/systems through specially crafted packet injections.
- Requires access to a victim's machine browser.
- Use browsers that support TLS 1.1/higher
Exploit:
Nmap: nmap -sV --script ssl-enum-ciphers -p 443 IPADDR
SLOWLORIS

CVE: CVE-2007-6750
A simple, yet powerful layer 7 (Application) DDoS (Distributed Denial-of-Service) attack created by Robert RSnake Hansen, named after the nocturnal primates that requires very little bandwidth. The attack has minimal-to-no side effects on services or ports and aims to disrupt a server's ability to respond to new requests from legitimate visitors. By passing normal looking HTTP requests, that are never completed while simultaneously receiving GET requests, these attacks can often bypass firewall and security measures, since they can be hard to spot.
Mitigation: Consists of having lower timeouts and accepting filtered buffer HTTP requests at the kernel level among other things.
Exploit:
Test:
Nmap: nmap --script http-slowloris-check IPADDR
Resources:
POODLE (Padding Oracle On Downgraded Legacy Encryption)

CVE: 2014-3566
Exploits vulnerabilities by downgrading SSL 3.0 handshakes, specifically targeting RC4, CBC and certain weaknesses in some TLS implementations. This allows attackers to gain access to sensitive data passed within encrypted web sessions (passwords, cookies, authentication tokens) which can be used to subsequently impersonate users. The vulnerability itself affects cipher suites that include symmetric encryption WITH block ciphers (AES/DES algorithms).
POODLE requires a 3 part-chain to be successful:
- MITM: The attacker has to listen to traffic between the target client/server AND be able to impersonate both (encryption makes this hard).
- The attacker has to convince the server to use the OLD SSL 3.0 protocol. This process often involves a tactic referred to as the "downgrade dance."
- When the client/server communicate with SSL 3.0, the attacker uses POODLE to decrypt selected parts of communication.
- Impacts: HTTPS that allows downgrades || SSL 3.0
Mitigation: Don't use SSL 3.0, RC4, or CBC
Exploit: https://github.com/thomaspatzke/POODLEAttack
Nmap: nmap -sV --version-light --script ssl-poodle -p 443 IPADDR nmap -sV --script ssl-enum-ciphers -p 443 IPADDR
Resources:

SWEET32

CVE: CVE-2016-2183 (3DES) || CVE-2016-6329 (Blowfish)
Sweet32 is a security vulnerability that targets ciphers using block ciphers, such as 3DES, or Blowfish, in SSL/TLS encryption. By exploiting these weaknesses an attacker could recover sensitive data within encrypted connections in web applications and services. To mitigate this, it's recommended to disable/phase out use of 3DES and other weak ciphers in favor of stronger encryption algorithms.
Mitigation: Avoid using legacy 64-bit block ciphers, and disable cipher suites using DES/3DES.
Exploit:
Test:
Nmap: nmap -sV --script ssl-enum-ciphers -p 443 IPADDR
Resources:
CRIME (Compression Ratio Info-Leak Made Easy)

CVE: 2012-4929
CRIME works by leveraging compression function properties in regards to the length of compressed data changes. This allows for a MITM attack that can obtain plaintext HTTP headers by observing length differences, in which a string in an HTTP request potentially matches an unknown string in an HTTP header.
- Protocols Impacted: HTTPS that use TLS 1.2/below
Mitigation: Upgrade to TLS 1.3
Exploit:

Resources:

BREACH (Browser Reconnaissance/Exfiltration Compression of Hypertext)

CVE: CVE-2013-3587
Leverages HTTP compression mechanisms rather than targeting TLS, like CRIME attacks. Unlike CRIME, it can be exploited even when TLS compression is turned off. To execute this successfully, an attacker redirects traffic to third-party URLs with TLS enabled, acting as a MITM. When web servers using HTTP compression inadvertently include user input/sensitive info in HTTP response bodies, they potentially disclose information.
Mitigation: Disable HTTP compression, randomize secrets per request and separate them from user input, length hiding and rate-limiting requests
Exploit:
Nmap:
Resources:

HEARTBLEED

CVE-2014-0160
I don't typically see this, but it was a fascinating critical vulnerability so I added it. The bug was discovered in the OpenSSL extension library responsible for maintaining connections and the flaw allowed connections to remain active as long as both parties were present. Clients sent heartbeat messages containing data to a server, and the server responded with the size of the data received. If an attacker manipulated the data length values sent to the server, in response, it unwittingly disclosed random data from memory, matching the length specified by the client.
To successfully exploit this:
- The site had to have SSL and a vulnerable version of OpenSSL (1.0.1-1.0.1f)
- Needed to be something useful in memory at the time of attack
Mitigation: Upgrade OpenSSL to the latest version, patch.
Exploit (Metasploit):use auxiliary/scanner/ssl/openssl_heartbleed

Nmap: nmap -p 443 --script ssl-heartbleed IPADDR
Resources:



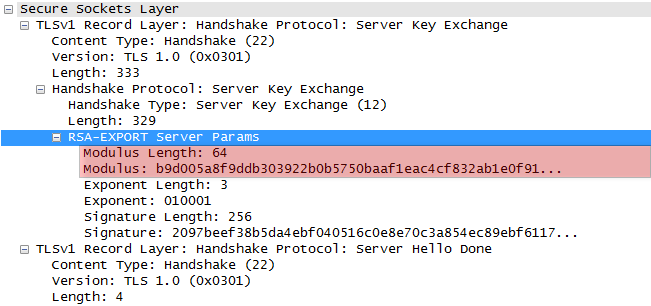
FREAK (Factoring RSA Export Keys)
Works by exploiting weak export cipher suites introduced to comply with government regulations. This attack manipulates the server into utilizing an export cipher suite with RSA moduli of 512 bits or less, which (which is easily cracked today).
Mitigation: Disable support for export-grade cipher suites
Nmap: nmap --script ssl-enum-ciphers -p 443 IPADDR
Resources:
- Refer to LOGJAM
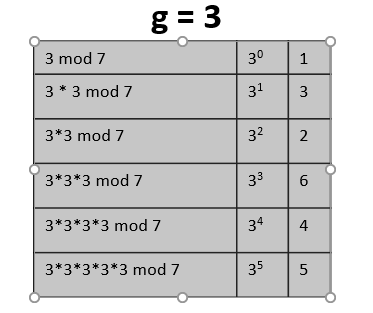
LOGJAM
CVE-2015-4000
A security vulnerability that permits attackers to intercept HTTPS connections by downgrading the connection to 512-bit, export-grade Diffie-Hellman groups. In essence, it is similar to the FREAK attack, but Logjam specifically targets the Diffie-Hellman key exchange mechanism instead of RSA's key exchange.
Mitigation: Disable export-grade cipher suites, use strong key exchange algorithms and enable PFS (Perfect Forward Secrecy) on servers.
Exploit:
Nmap:nmap --script ssl-dh-params IPADDR
Resources:

In Part 1 of this series, we discussed fundamental attacks commonly encountered in pentests, along with valuable resources. Two highly effective nmap scripts for assessing various vulnerabilities are --script ssl-enum-ciphers and --script vuln (not to be confused with vulners which is also worth noting).
In upcoming sections, we'll delve further into recommended tools such as sslscan, testssl.sh, cipherscan, and curl to enhance our understanding and response to these security challenges. We'll also explore and address common certificate-related issues that frequently emerge during pentests. Certificates play a crucial role in securing web communications, and understanding how to test, validate and resolve issues is a good way to improve posture.
This concludes Part 1 of the series











